If you ever had any questions about the value of cyber security, you can find 73 million names and personal data of AT&T customers who are now convinced.
Hackers hacked the files, which contained just about everything one doesn’t want to be released: SIN, name, address, etc. and likely banking information. The import of this pantomime can’t be overstated; It is very, very bad.

While the breaches vary for each customer affected, AT&T says that information involved in this leak included social security numbers and passcodes — which, unlike passwords, are numerical PINS that are typically four digits long. The company said that it was likely that full names, email addresses, mailing addresses, phone numbers, dates of birth, and AT&T account numbers may also have been compromised. It added that the data affected is from 2019 or earlier and does not appear to include financial information or call history.
I have mentioned the importance of exposure to the cybersecurity sector before. There is even a couple of cybersecurity ETFs with catchy symbols such as “BUG and HACK.”
According to a report by Global Market Insights, the cybersecurity market has an expected compound annual growth rate of 15% through 2032 and is forecast to reach a market size of about $900 billion.
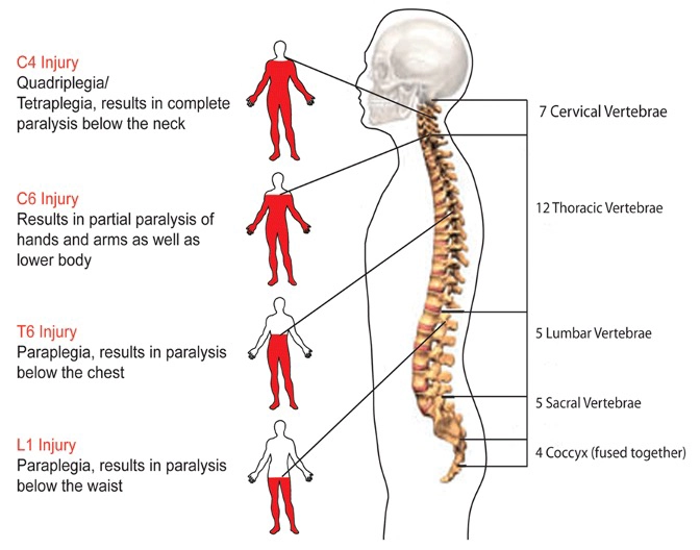
The Global X Cybersecurity ETF (BUG) is an exchange-traded fund based on the Indxx Cybersecurity index, a modified market-cap-weighted global index of companies selected based on revenue related to cybersecurity activities. BUG was launched on October 25, 2019, and is managed by Global X. The 52-week range is USD 21.00 to USD 32.00.
While an ETF may be the easy way out, hooking up with some promising juniors may yield better returns. It may also keep investors on the cutting edge and development of tech new processes that could potentially cause positive price movements, takeover potential, or even decent ongoing returns.

Integrated Cyber (ICS) is such a stock. The Company is a managed security service provider (MSSP) that humanizes cybersecurity managed services to the Small-to-Medium Business (SMB) and Small-to-Medium Enterprise (SME) sectors.
While the stock has weakened lately, several historical price and volume spikes have occurred. While the volume is light but growing, a purchase of ICS serves two purposes: a proxy for the cyber security market and potentially a partnership or takeover target as the tech progresses and new developments ensue. If you’d like to see a selection of nasty cyber attacks, ICS has compiled a list of recent attacks. Some are simply breathtaking.
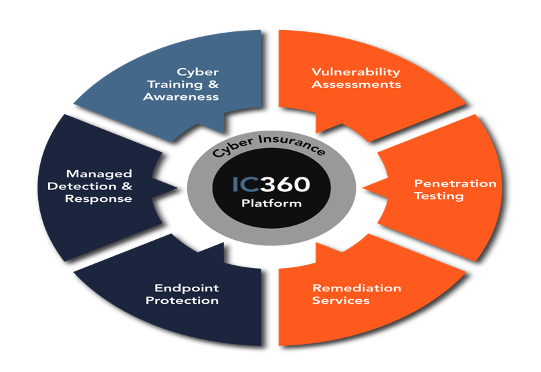
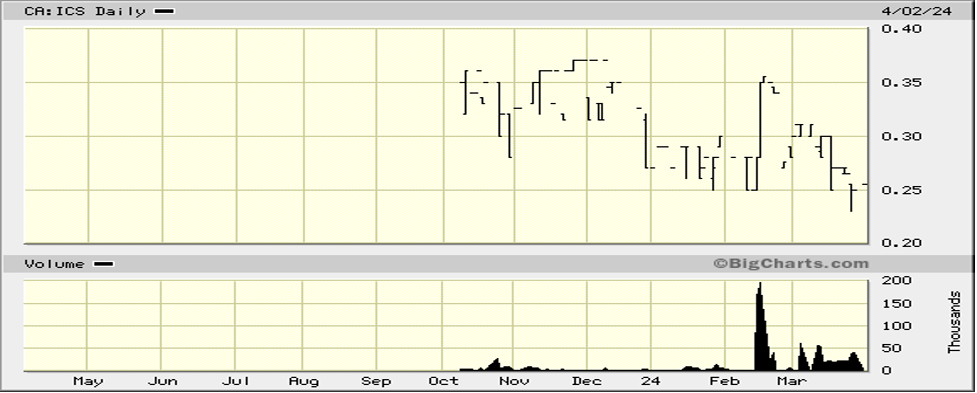
The key to ICS’s current offerings in the space is its 360 platform.
Managing ‘horizontally’ across a complex cyber technology stack can be overwhelming. However, with IC360’s advanced Security Orchestration and Automation integrations, you can quickly secure your entire stack with just one platform.
Latest News
JV with HSG Middle East, a member of the Gulf Cooperation Council (GCC), with relationships a member of the Gulf Cooperation Council (GCC), with relationships totalling over 500 hotels and 55,000 rooms in the region totalling over 500 hotels and 55,000 rooms.
Through this partnership, the Company anticipates gaining access to local market insights, cultural nuances, and regulatory knowledge essential for navigating and participating in this unique regional landscape.
HSG Holding was established to focus on investment opportunities within the hospitality sector at the intersection where the strength of traditional hospitality operations meets with new technologies that can assist in the digital transformation of the industry. Technology plays a far more significant role in the industry and quickly becomes a critical aspect of hotel operations. The company believes in investing over the long term as it sees significant opportunities for growth in the MEA region and beyond.
“Strong networks and the ability to implement the latest wired and wireless technologies is what gives our customers the edge over their competitors. It means that guests staying in their hotels are able to connect to the internet effortlessly, access streaming services such as Netflix, and even call the concierge from their own mobile device, rather than relying on in-house telephone services. The hotel’s Guest Relations team is able to welcome guests and keep them informed about available services and activities as well as updated airport arrivals and departure times via in-house advertising and promotions across a variety of dynamic information points,” says Olivier Hennion, Managing Director of IT Hospitality Group. While HSG is not AT&T, the scope of this JV opens the hotel/hospitality sector to ICS. Its tech will protect clients from cyber threats while at the hotel facility. The plan is robust and should increase ICS’s global profile.
• Collaborate with the UAE Government to develop a credentialing system tailored for individuals, corporations, and government agencies within the UAE
• Maintain focus on delivering cyber services to the power generation industry. It is anticipated that ICS Middle East will be in contention to provide cyber services to a power plant supplying approximately 20% of Dubai’s electricity
• Offer cyber services to existing hotel and hospitality clients of HSG,
• Establish a partnership with a leading provider of critical IT services and hardware to the UAE healthcare sector
• Capitalize on the momentum created by HSG’s new office in Riyadh, Saudi Arabia, with plans to replicate the successful approach in the UAE by providing cyber services to hospitality, healthcare, and governmental sectors.
In its last PR, the company announced a repeat customer, which is, in some ways, better than a new client.
Why? One word: VALIDATION.
Revolutionize Your Cybersecurity with IC360
Say goodbye to segmented cybersecurity and hello to a comprehensive solution with IC360, a platform that helps you secure your cyber technology stack by cross-correlating information across multiple siloed software and hardware solutions. This allows you to see the big picture and identify potential threats your team may not see by only looking at one application.

Bob Beaty
For over 30 years, Bob Beaty has been explaining concepts and companies to the global investment community. One of the original writers for Jim Cramer’s Thestreet.com, he also wrote for AOL (Can/US), the Globe and Mail, and the Huffington Post. Over that period, he illuminated small-cap companies to investors with wit and pith but mostly opinion and facts. Investing should be fun. Pedantic, staid content is no fun.
Before embarking on his writing career, Bob had a successful international journey in the finance industry. He served as a broker, derivatives product manager, and a Director of London's Credit Suisse subsidiary. His career spanned across major financial hubs including Toronto, Vancouver, and the UK, giving him a unique global perspective. (He is still fondly remembering those English client lunches.)
Other than everything Groucho Marx and George Carlin ever said, Bob lives by a simple credo;
‘Never do anything the person standing in front of you can't understand.’ Hunter S. Thompson.
Let’s go.